よむ、つかう、まなぶ。
参考資料4_Action plan for whole genome analysis 2022 (41 ページ)
出典
| 公開元URL | https://www.mhlw.go.jp/stf/newpage_35569.html |
| 出典情報 | 厚生科学審議会 科学技術部会全ゲノム解析等の推進に関する専門委員会(第17回 10/3)《厚生労働省》 |
ページ画像
ダウンロードした画像を利用する際は「出典情報」を明記してください。
低解像度画像をダウンロード
プレーンテキスト
資料テキストはコンピュータによる自動処理で生成されており、完全に資料と一致しない場合があります。
テキストをコピーしてご利用いただく際は資料と付け合わせてご確認ください。
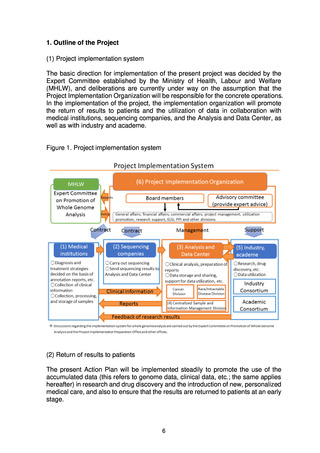
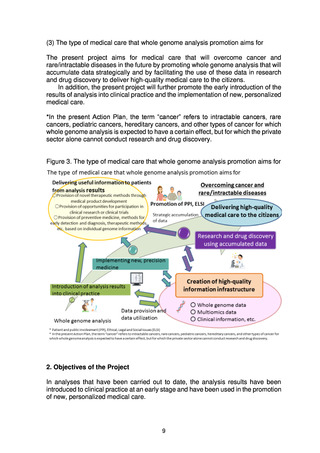
Data management and system creation within the Data and Analysis Center
are important infrastructure that relate directly to the treatment of patients.
It is therefore important to control access to the data, manage the logs,
store the data safely using secret sharing technology, and implement a
security detection and decision-making process. It will thus be necessary
to satisfy the following requirements relating to data management, data
storage, system development and environment creation, and security.
• Data management
Access to clinical information and genome data is strictly managed
not just by logs, but also by management of data users (who is given
access to which data, and when, etc.).
• Data storage
Data are stored in a form that is sufficiently secure. This requires
investigation of multiple technologies such as secret sharing
technology to ensure use of the optimal technology, as well as a
constant grasp of issues such as interoperability and scalability.
Both on-premise and partial cloud storage will be verified in FY2022
for storage of genome data. From FY2023 onward, storage will be
implemented as a hybrid operation that takes into account the
strengths and weaknesses of both of them.
• System development and environment creation
An analysis workflow from primary analysis to secondary analysis and
diverse analysis resources will be provided using a hybrid on-premise
and cloud framework.
Secure systems and a secure network environment will be put in place
between medical institutions, sequencing companies, and the
Analysis and Data Center. The Analysis and Data Center will be
based on the use of servers physically located in Japan.
The information system will be created in a highly scalable form so
that it is not dependent on any specific technology and can constantly
incorporate new technologies.
• Security requirements
The cloud is to be registered or in the process of registration with
ISMAP (the Japanese government’s Information System Security
Management and Assessment Program). Firewalls will be deployed
in the cloud for security monitoring, detection, and blocking.
The system must be capable of monitoring and reporting suspicious
behavior through storage of data access logs and correlation analysis
rules using these logs. Methods will be examined to automatically
perform periodic optimization of correlation analysis to prevent false
positives.
For security detection, the payload (contents of packet transmission
passing through the network) of cloud services has log-based
monitoring that cannot be checked or detected, and it is therefore not
fully real-time monitoring. Methods to avoid this will be examined.
Automation of the security decision-making process to quickly isolate
the system, take countermeasures, and make a report after an
incident occurs, as well as methods to avoid false positives and overdetection, will be examined.
40
are important infrastructure that relate directly to the treatment of patients.
It is therefore important to control access to the data, manage the logs,
store the data safely using secret sharing technology, and implement a
security detection and decision-making process. It will thus be necessary
to satisfy the following requirements relating to data management, data
storage, system development and environment creation, and security.
• Data management
Access to clinical information and genome data is strictly managed
not just by logs, but also by management of data users (who is given
access to which data, and when, etc.).
• Data storage
Data are stored in a form that is sufficiently secure. This requires
investigation of multiple technologies such as secret sharing
technology to ensure use of the optimal technology, as well as a
constant grasp of issues such as interoperability and scalability.
Both on-premise and partial cloud storage will be verified in FY2022
for storage of genome data. From FY2023 onward, storage will be
implemented as a hybrid operation that takes into account the
strengths and weaknesses of both of them.
• System development and environment creation
An analysis workflow from primary analysis to secondary analysis and
diverse analysis resources will be provided using a hybrid on-premise
and cloud framework.
Secure systems and a secure network environment will be put in place
between medical institutions, sequencing companies, and the
Analysis and Data Center. The Analysis and Data Center will be
based on the use of servers physically located in Japan.
The information system will be created in a highly scalable form so
that it is not dependent on any specific technology and can constantly
incorporate new technologies.
• Security requirements
The cloud is to be registered or in the process of registration with
ISMAP (the Japanese government’s Information System Security
Management and Assessment Program). Firewalls will be deployed
in the cloud for security monitoring, detection, and blocking.
The system must be capable of monitoring and reporting suspicious
behavior through storage of data access logs and correlation analysis
rules using these logs. Methods will be examined to automatically
perform periodic optimization of correlation analysis to prevent false
positives.
For security detection, the payload (contents of packet transmission
passing through the network) of cloud services has log-based
monitoring that cannot be checked or detected, and it is therefore not
fully real-time monitoring. Methods to avoid this will be examined.
Automation of the security decision-making process to quickly isolate
the system, take countermeasures, and make a report after an
incident occurs, as well as methods to avoid false positives and overdetection, will be examined.
40